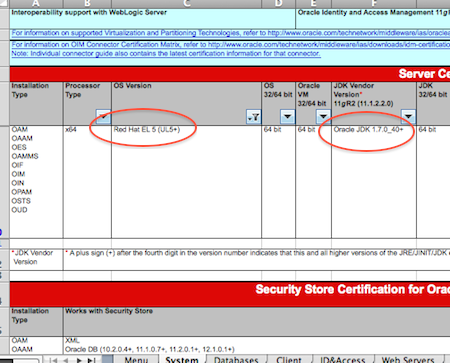
I recently configured access control in OID to grant READ/WRITE access on one of the OU in OID to a group. This post cover steps to debug Access Control issues (READ/DELETE/MODIFY) in OID.
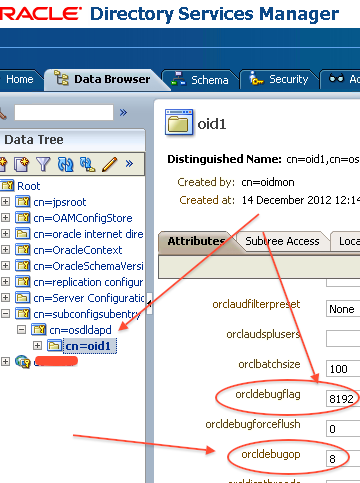
- If you encounter “Insufficient Access Rights” in OID then enable Debug in OID (Set orcldebugflag to 8192 and orcldebugop to 8 to OID instance) using ODSM
Note: For value of orcldebugflag (8192 is for Access Control List Processing) & orcldebugop (8 is for DELETE ) follow Note # 1239943.1 How To Set OID Debug / Trace Levels for 11g
![oid_debug_1]()
Replicate issue and check OID logs at $ORACLE_INSTANCE/ diagnostics/ OID/ oid/ oidldapds[NNNNN].log
_______
2014-01-23T23:45:00+00:00] [OID] [TRACE:16] [] [OIDLDAPD] [host: oidhost.oiddomain] [pid: 17878] [tid: 10] [ecid: 004wAjKOjRu6aMW_Lxo2ye0004NM00001V,0] ServerWorker (REG):[[
BEGIN
ConnID:77 mesgID:34 OpID:33 OpName:delete ConnIP:192.168.1.12 ConnDN:cn=atul kumar,ou=internal,cn=users,dc=onlineappsdba,dc=com
gslaudegGetNearestACP:Parsing the node cn=testuser1,ou=external,cn=users,dc=onlineappsdba,dc=com
2014-01-23T23:45:00 * gslaudegGetNearestACP:Parsing the node ou=merchant users,ou=testou,ou=external,cn=users,dc=onlineappsdba,dc=com
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Operation id:(33) Entry DN: (cn=testuser1,ou=external,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation: Operation id:(33) User DN: (cn=atul kumar,ou=internal,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (ou=users,ou=testou,ou=external,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (ou=testou,ou=external,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (ou=external,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Entry Accees denied by ACP:(cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Operation id:(33) User has Privilege groups Evaluation continues
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Entry Accees denied by ACP:(dc=onlineappsdba,dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Operation id:(33) User has Privilege groups Evaluation continues
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Entry Accees denied by ACP:(dc=com)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Operation id:(33) User has Privilege groups Evaluation continues
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (cn=root)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Entry Accees denied by ACP:(cn=root)
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Operation id:(33) User has Privilege groups Evaluation continues
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Op id:(33) Enforcing Server Def Access Policy
2014-01-23T23:45:00 * gslaudeeEntryEvaluation:Operation id:(33) Access to Entry (cn=testuser1,ou=External,cn=Users,dc=onlineappsdba,dc=com) not allowed by ACP at: (Deafault Policy)
END
]]
_______
If you notice Access Control Policy checked it all the way from ou=external,cn=users,dc=onlineappsdba,dc=com –> cn=users,dc=onlineappsdba,dc=com –> dc=onlineappsdba,dc=com –> dc=com –> cn=root
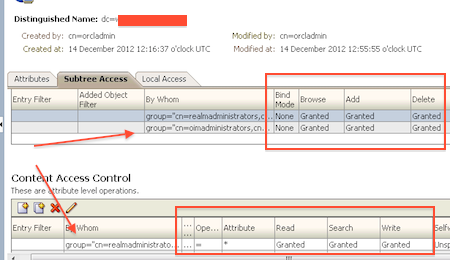
Fix: I defined ACL at level dc=onlineappsdba,dc=com and granted access to group “cn=oimadministrators…” and added user cn=atul kuma…. to group cn=oimadministrators
- For more information on ACL in OID 11g click here
![acl_2]()
Log after defining ACL
_______
2014-01-23T23:45:00+00:00] [OID] [TRACE:16] [] [OIDLDAPD] [host: oidhost.oiddomain] [pid: 17878] [tid: 10] [ecid: 004wAjKOjRu6aMW_Lxo2ye0004NM00001V,0] ServerWorker (REG):[[
BEGIN
ConnID:77 mesgID:34 OpID:33 OpName:delete ConnIP:192.168.1.12 ConnDN:cn=atul kumar,ou=internal,cn=users,dc=onlineappsdba,dc=com
gslaudegGetNearestACP:Parsing the node cn=testuser1,ou=external,cn=users,dc=onlineappsdba,dc=com
2014-01-23T23:59:00 * gslaudegGetNearestACP:Parsing the node ou=merchant users,ou=testou,ou=external,cn=users,dc=onlineappsdba,dc=com
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Operation id:(33) Entry DN: (cn=testuser1,ou=external,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:59:00 * gslaudeeEntryEvaluation: Operation id:(33) User DN: (cn=atul kumar,ou=internal,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (ou=users,ou=testou,ou=external,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (ou=testou,ou=external,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (ou=external,cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Op id:(33) Entry Accees denied by ACP:(cn=users,dc=onlineappsdba,dc=com)
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Operation id:(33) User has Privilege groups Evaluation continues
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Op id:(33) Visiting ACP at: (dc=onlineappsdba,dc=com)
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Op id:(33) Enforcing Server Def Access Policy
2014-01-23T23:59:00 * gslaudeeEntryEvaluation:Operation id:(33) Access to Entry (cn=testuser1,ou=External,cn=Users,dc=onlineappsdba,dc=com) allowed by ACP at: (dc=onlineappsdba,dc=com)
END
]]
_______
References
Related Posts for OID
- Oracle Internet Directory OID
- Oracle Internet Directory – Basics II
- OID to OID/Active Directory/iPlanet other LDAP Server Integration
- Multi Master OID Replication
- OID Architecture
- Oracle Internet Directory , OID Troubleshooting
- Server Chaining in OID
- OID Quesries/ Scripts FAQ
- OIDADMIN Client
- Oracle Identity Management (OID) 11g installation Issues on Linux
- OID 11g – Oracle Directory Services Manager (ODSM)
- DIP : Synchronization, Provisioing, Connectors, DSS in Oracle Directory Services (ODS) 11g
- OID Replication – Suppliers, Consumers, DRG, ASR/LDAP based replication
- ASR setup has failed – Error occurred while dropping database link : ORA-02084 : database name is missing a component while Configuring Multi Master OID replication using “remtool -asrsetup”
- OID 11g Down : Unable to Start OID 11g using OPMN (ODS schema locked ORA-28002)
- OID/Directory Services 11g – Schema, Object Class, Attributes
- OID 11g Distributed Install : DIP/ODSM (Java Component) & OID (LDAP/REPLD) on different machine
- OID Server Mode R, RW, RM: LDAP: error code 53 – Server currently in read only mode
- How to change OID 11g database schema (ODS) password
- How to add custom attribute, Object Classe in OID from command line or GUI
- Oracle Internet Directory (OID) and Real Application Cluster (RAC) database : Things you must know
- How to Update User Password in OID (single account or bulk) – command line or GUI
- Error starting OID 11g during configuration stage of OID installation on Windows Server “ProvisionException: Failed to start the component”
- How to delete Entries in OID 11g in Bulk – Delete Failed : Ldap Error Code 66 Not allowed on Non-Leaf
- How to find latest changelog number (or changes) in OID ?
- Context Initialization Error on running ldapsearch commands on OID Server
- How to find OID version and patches applied on OID Home ?
- How to change OID 11g LDAP/LDAPS listen port
- How to find/audit Failed Login Attempts in OID 11g
- Step by Step configuration of OID Multi Master Replication – LDAP based in OID 11g
- OID 11g LDAP based Multi Master replication : Configuration Entries you must know
- Configure SSL for Oracle Internet Directory (OID)
- How to backup Oracle Internet Directory (OID) 11g – Data : Full / Partial
- SSL / Wallets in OID/OHS : How to manage certificates in Wallet using command line ?? ORAPKI
- How to debug OID : LDAP Error code 50 – Insufficient Access Rights